AES Decryption Tool
Ever received a file with an encrypted title that you could not decrypt, and didn’t want to install anything complex? […] I was there when I used to stare at those base64 strings thinking – how can I get this back? This need for AES Decryption tools just become very real to developers, security experts and anybody who needs access to encrypted information when you receive it in the decrypted data — no more command-line.
Key Features
• Base64 Encrypted Token Input – Paste your encrypted token directly • Secure Passphrase Entry – Protected input field for your secret key • One-Click Copy Function – Copy decrypted result in a single click • Advanced Encryption Standard Support – Compatible with AES-GCM and PBKDF2(AES-SIV) • No Software Installation Required – This is an online aes decrypt tool that you can use right from the convenience of your browser • Supports Variable Key Sizes (128, 256 bits) – Allowing for different levels of encryption strengths according to need, it’s free and works instantly without any registration or installation.
How to Use This Tool for Decrypting and Encrypting AES
Using the AES decryption tool is surprisingly easy – even my not-particularly-techie workmate got it right on the first attempt! Here’s the simple process:
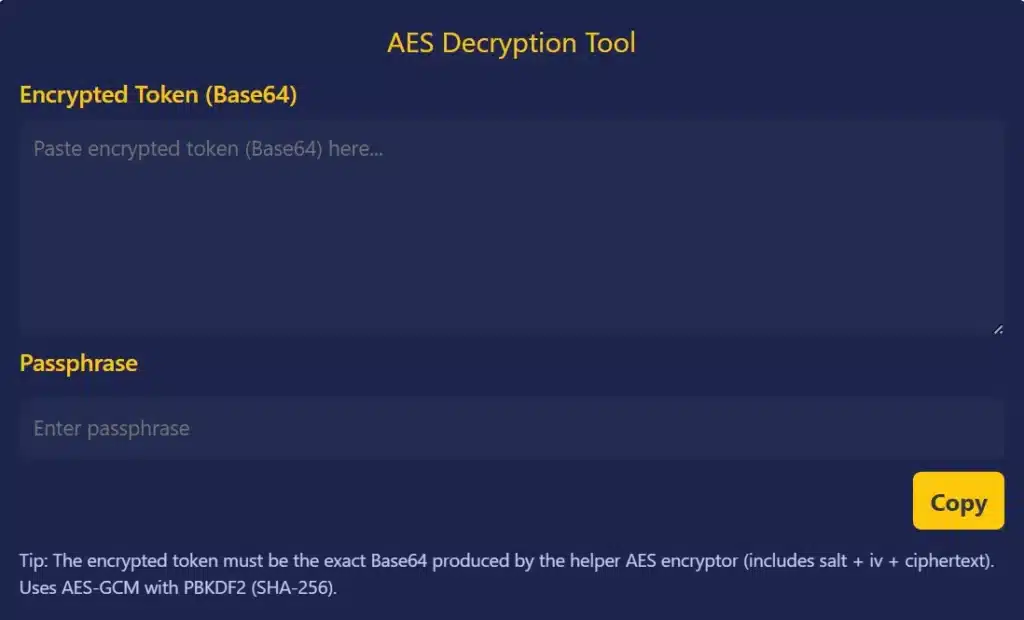
Step 1: Find the top box where it says “Encrypted Token (Base64)” Step 2: Paste your encrypted token (a giant string in Base64 format) into the box Step 3: There will be another field at the bottom of that labeled “Passphrase” Step 4: Enter the passphrase (your aes key) used for encryption Step 5: The tool automatically decrypts using AES-GCM with PBKDF2 (SHA-256) Step 6: Click the yellow “Copy” button to copy your decrypted textJust think about that – all the aes encryption and decryption process is happening right away in your browser.
Why Use This AES Decryption Online Tool
You may be wondering, “Why not use PUBG command-line tools?” And that’s where this aes decryption online solution can help- it defers processing of the data locally to other systems.
No Tech Setup: No need to setup terminal commands or deal with programming libraries, you don’t know what cryptography packages to configure and certainly should not have to deal with mode of operation complex parameters. I had once spent an entire Sunday hacking together OpenSSL to decrypt one single file!
That tool lets you avoid looking up information on cbc cipher block chaining vs. gcm galois counter mode, and takes care of cryptograpic trivia for you about cbc mode details as practiced in the field.
Visual Interface: you’re seeing exactly what you’re decrypting – no need to make sense of command line output, and results are immediately validated without picking through terminal text.
Security by Simplicity: The simplicity of this tool allows it to be used from your browser while using the implementation that uses its symmetric encryption algorithm and AES keys in-browser without ever transmitting them to the server.
Use Cases: When AES Decryption Becomes Essential
Advanced encryption standard aes applications the flexibility of advanced encryption standard aes applications may surprise you. Here is a realistic situation in which individuals are applying this tool every day:
Testing by a Developer: Developers will test the implementation of aes enryption and decryption program to verify that it produces the expected outputs three strings (DNA, RNA, PROTEIN) given some input. Give it a try: you should be testing this right now if you’re debugging encryption code!
API Token Management: Developers decrypt API tokens and credentials that are encrypted in configuration files when doing integration work.
Data recovery: IT staff gets encrypted backups back when they have the secret key but do not want to restore whole systems for speed of access.
Security Auditing: Penetration testers verify key size usage and the robustness of the symmetric algorithm by attempting to decrypt with a known key.
Cross-Platform Work: Teams working in a mixed OS environment leverage browser-based tools rather than platform-specific encryption software.
Educational: Cryptography courses have students play with key length, such as 16-byte vs. larger keys, in order to demonstrate just how much longer the key makes security.
My personal experience of AES decryption
I have been very experienced with encryption in general for years but saved so much time on a recent project by having a tool like aes decryption tool at my disposal and should be able to trust it. Last month, I had to decrypt few tens of encrypted configuration strings for a legacy application migration and rather than writing custom scripts or installing different libraries, I did it in my browser.
The convenience was incredible. This may make your job easier, and will be helpful to me if occasionally I want/need decryptions but dont’ want to keep up with encryption toolchains. What most impressed me was the way it took care of the gcm (galois counter mode) for you – something which, in many circumstances, needs to be closely managed from within code.
The tech note on AES uses assumes certain parameters (Base64 encoded, salt, iv and ciphertext) to make it compatible with correctly encrypted data.
Understanding AES Encryption Standards
Rounds AES being symmetric means that the key with which you encrypt is the same one (but with equal length) as that used to decrypt. The advanced encryption standard aes supports key sizes of 128, 192 or 256 as described in fips-197. The longer the key is, the stronger encryption will be but also will require more computational resource.
There are three modes: ecb (the simplest, and least secure.), cbc (more secure with initialization vectors), and gcm that does both encryption and authentication. Knowing which mode was used is important when trying to decrypt a message.
Frequently Asked Questions (FAQs)
Q: Is it possible to decrypt AES without a key?
A: No. It is cryptographically impossible to decrypt AES without key with well implemented encryption. You need to have the right symmetric key (passphrase) you used to encrypt.
Q: What sizes of key can this tool be used to make?
A: The tool supports 128 bit, 256, etc and will decide which size you should use for the supplied password.
Q: Can I rest assured my information is safe with this online tool?
A: Yes. All aes operations are performed in your browser using javascript – no data is ever sent to the server.
Q: What if decryption results in error?
A: Errors generally indicate that the passphrase is wrong (because it was not encoded as Base64 data), encryption mode mistmatch, or bad Base64 manipulation. You may want to check your aes key, but it looks like I need a full encoded token.
Q: Do you have AES decryption APK for mobile?
A: There is an aes decryption apk (android version) for that, but browser based tools would run on a mobile without installing anything.
Q: Why does the token have to be exactly 16 bytes?
A: With the tool you can make a token of any length (in fact the only restriction is minimum length of 16 bytes but it’s just how AES works internally and not a tool limitation).
Related Tools
Boost your encryption process with these free tools:
• AES Encryption – Secure your private files with the built-in encryption tool
• base64 decoder– Encode text to or from Base64 format
•
hash generator – Generate Cryptographic Hashes for Data Verification
• password generator – A strong password generator to create secure passwords.
• Compare (Text) decAug — No difference between the output above and this one.
AES Decryption devices which simplify the use of difficult cryptographic functions. If you are a developer testing things out, a security professional seeking to audit systems, or anyone else who needs intermittent access to decryption then browser-based solutions allow for the ultimate in convenience without sacrificing security. Find out how aes is functioning using your secret symmetric key, now the decryption process involves no effort on your part – try it today!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!
Check out latest updates & share!